Network Security & Cloud Network Security
Safeguard Your Digital Perimeter, On-Premise and in the Cloud.
In today’s borderless digital landscape, your network is no longer confined to four walls. It extends from your corporate office to remote employees and across multiple cloud environments. This expanded attack surface demands a new, unified approach to security.
[Your Company Name] provides comprehensive Network Security and Cloud Network Security solutions designed to protect your data, applications, and users wherever they are. We build resilient, intelligent defenses that enable your business to operate securely and at speed.
The Modern Challenge: Your Network is Everywhere
Is your security strategy keeping up?
Are your remote users a backdoor into your core network?
Is data securely segmented in your cloud environments (AWS, Azure, GCP)?
Can you consistently enforce policies across hybrid infrastructure?
Are you protected against evolving threats like ransomware and zero-day exploits?
Traditional perimeter-based security is no longer enough. We help you build a secure, agile, and cloud-native network foundation.
Our Network Security Services
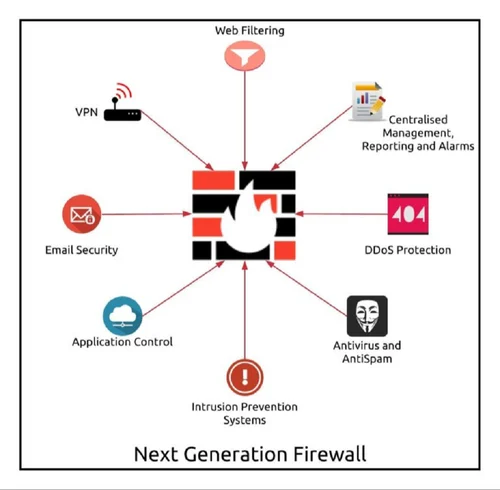
Next-Generation Firewalls (NGFW)
It’s not just about ports and protocols anymore. Modern threats hide in encrypted traffic, malicious apps, and sophisticated attacks.
A Next-Generation Firewall (NGFW) does what old firewalls can’t:
✅ Deep Packet Inspection – Reads the content of data.
✅ Application Control – Blocks risky apps (even ones using “allowed” ports).
✅ Integrated IPS – Stops attacks in their tracks.
✅ Threat Intelligence – Learns from global threats to protect you.
Stop just blocking doors. Start intelligently guarding your castle.
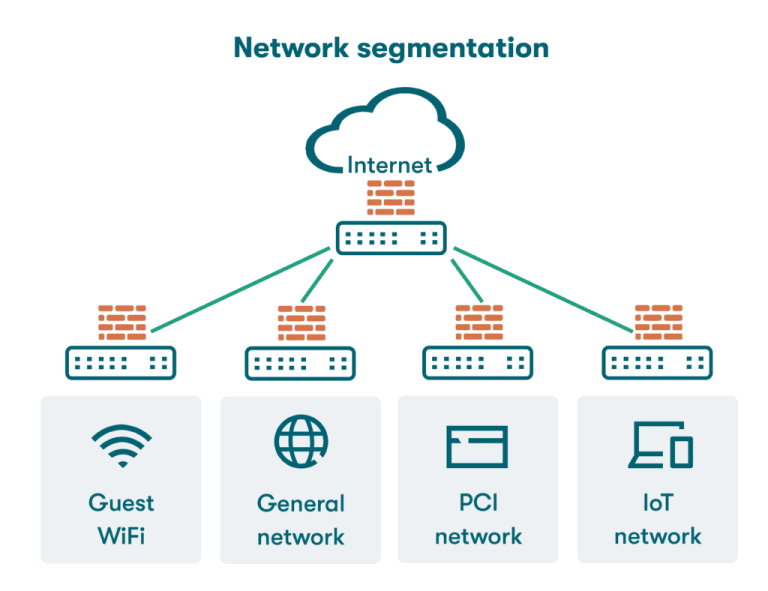
Secure Network Architecture & Segmentation
In today’s threat landscape, a flat network where every device can talk to every other device is a high-risk liability. A single breach can lead to catastrophic data loss and operational downtime.
Secure Network Architecture & Segmentation is the strategic practice of dividing your network into isolated, controlled segments. It’s about building internal walls and checkpoints, so even if attackers get in, they can’t move freely to your crown jewels.
.
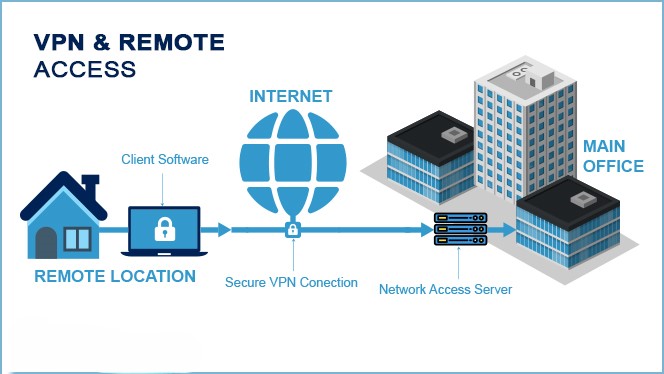
VPN & Secure Remote Access
In today’s digital world, employees often need to access company resources (like files, applications, and internal networks) from outside the office. Secure Remote Access is the overarching practice of providing this access safely and securely.
A Virtual Private Network (VPN) is the most common tool used to achieve this.
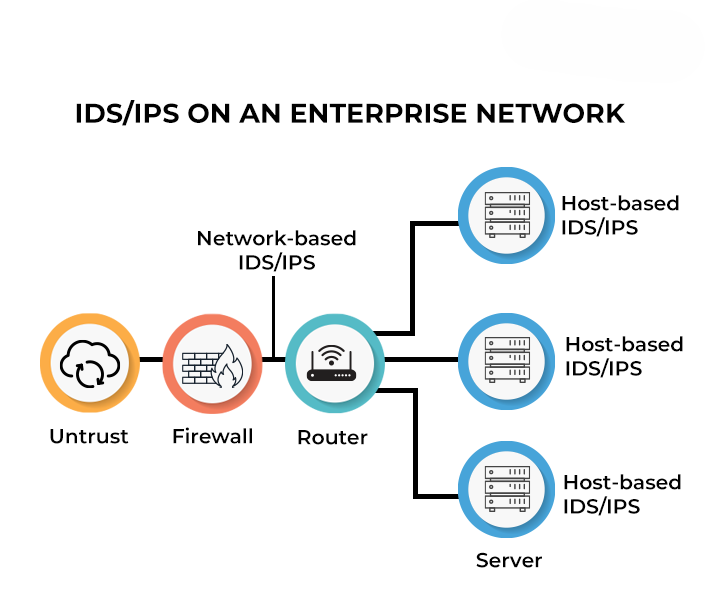
Intrusion Detection & Prevention Systems (IDS/IPS)
In today’s threat landscape, a simple firewall isn’t enough. Cyberattacks are evolving fast, and your network needs a vigilant guardian. That’s where Intrusion Detection and Prevention Systems (IDS/IPS) come in. Think of them as your 24/7 digital security team, constantly monitoring traffic to identify and stop malicious activity.